In an increasingly digital world, where businesses rely heavily on a multitude of software applications, managing user authentication across different platforms has become a significant challenge. This is where Single Sign-On (SSO) comes into play. SSO is a user authentication process that allows an individual to access multiple applications with a single set of login credentials. It simplifies the management of multiple usernames and passwords while enhancing security and user experience.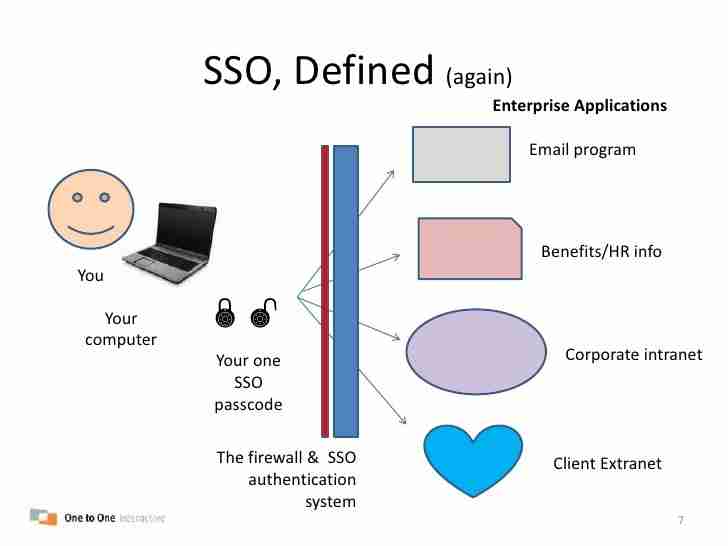
What is Single Sign-On (SSO)?
Single Sign-On (SSO) is an authentication method that enables users to log in once and gain access to multiple applications and systems without being prompted to log in again at each one. This process is particularly beneficial in environments where users need to switch between various applications frequently, such as in corporate settings, educational institutions, and e-commerce platforms.
How Does SSO PORTAL Work?
SSO PORTAL works by utilizing a centralized authentication server that communicates with multiple applications or services. When a user logs in through the SSO portal, the authentication server verifies the user's credentials. Once authenticated, the server generates a token or session that is passed along to the other applications or systems the user wants to access.
Here’s a simplified workflow of how SSO operates:
- User Authentication: The user enters their login credentials (username and password) into the SSO portal.
- Verification: The SSO system verifies the credentials against a centralized authentication database, such as an Active Directory or LDAP.
- Token Generation: Upon successful authentication, the SSO server generates an authentication token or session cookie.
- Token Sharing: This token is shared with the other applications or services the user needs to access.
- Access Granted: The user can access the linked applications without needing to log in again, as long as the token remains valid.
Benefits of SSO
SSO offers numerous benefits for both users and organizations:
Enhanced User Experience: SSO significantly improves the user experience by reducing the need to remember and manage multiple passwords. Users log in once and gain seamless access to all their applications, reducing frustration and saving time.
Increased Productivity: With SSO, users can switch between applications quickly, without the constant need to log in, which enhances productivity. This is especially important in environments where time and efficiency are critical, such as healthcare or finance.
Improved Security: While it may seem counterintuitive, SSO can enhance security by reducing the likelihood of weak password practices. Since users need to remember only one password, they are less likely to reuse passwords or resort to easy-to-guess combinations. Additionally, SSO systems often incorporate multi-factor authentication (MFA), adding an extra layer of security.
Centralized Control: SSO provides IT administrators with centralized control over user access to various applications. This makes it easier to enforce security policies, monitor user activity, and manage permissions. If a user’s access needs to be revoked, it can be done quickly across all applications.
Reduced IT Costs: Managing a large number of passwords can be a significant burden on IT support teams. SSO reduces the number of password-related issues, such as resets, which in turn lowers the overall IT support costs.
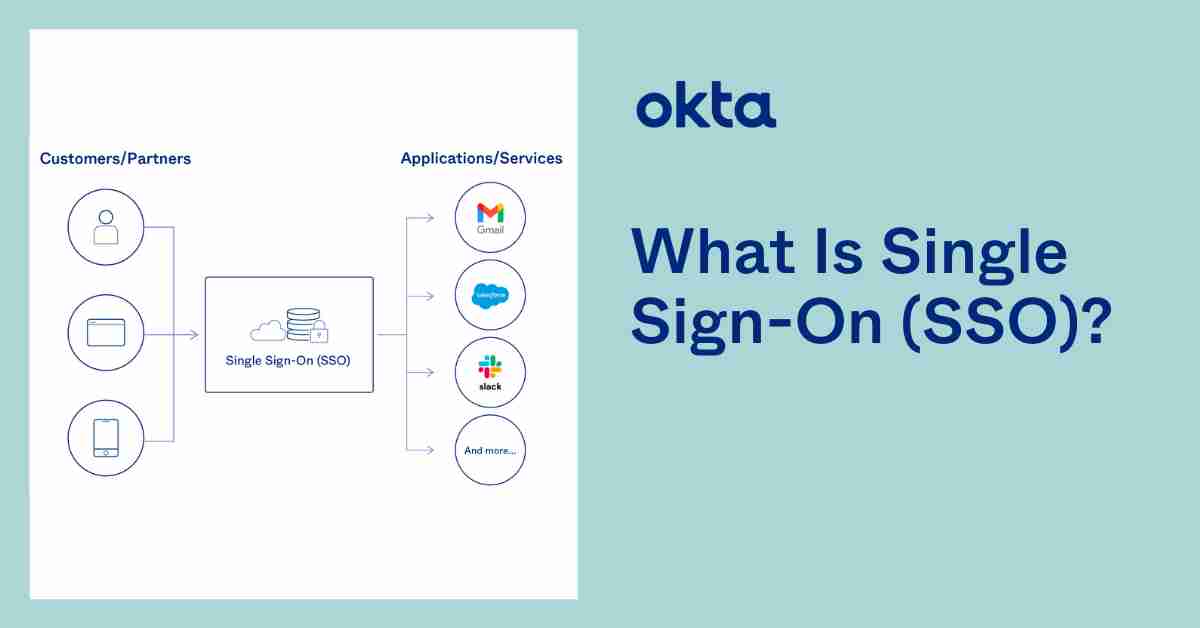
Challenges and Considerations
Despite its many advantages, SSO is not without its challenges:
Single Point of Failure: The biggest risk associated with SSO is the single point of failure. If the SSO system goes down, users may lose access to all connected applications. This makes it critical to implement robust redundancy and failover mechanisms.
Security Risks: While SSO can enhance security, it also presents risks. If a user's SSO credentials are compromised, the attacker could gain access to all linked applications. Implementing strong authentication methods and monitoring for unusual activity is essential.
Complex Implementation: Setting up an SSO system can be complex, especially in environments with a mix of legacy and modern applications. It requires careful planning, configuration, and testing to ensure compatibility across all platforms.
Integration Issues: Not all applications support SSO out of the box, which can lead to integration challenges. Organizations may need to invest in custom development or third-party solutions to bridge the gaps.
Conclusion
Single Sign-On is a powerful tool that addresses the growing need for efficient and secure user authentication in today’s digital landscape. By simplifying the login process and centralizing user management, SSO enhances the user experience, boosts productivity, and strengthens security. However, like any technology, it requires careful implementation and management to mitigate potential risks and maximize its benefits. As businesses continue to adopt more applications and cloud services, the role of SSO in ensuring smooth and secure access will only become more crucial.



